Summary: Generally available today, VMware NSX for vSphere 6.4 raises the bar for application security and planning, and introduces context-aware micro-segmentation
For those working in security, thinking and talking about the cyber threats in the world is a constant, a necessary evil. So, for a moment, let’s summon a better time to our memory. Remember when breaches didn’t keep us up at night? The threat of a breach didn’t hang over our heads with an associated cost of millions of dollars and the privacy of our users. In fact, it did, but they weren’t frequent or public enough to cause the awakening that they do today. We put up a wall at the perimeter to keep the bad guys out, and prayed.
OK, back to modern times. Today, we know the story is much different, for better and for worse. Breaches are more prevalent, but our defenses are more sophisticated and more importantly, they’re continuously evolving (just like the breaches). One major piece of this newer defense picture is micro-segmentation. With micro-segmentation, security policies traditionally only enforced at the perimeter are now brought down to the application. Micro-segmentation has gained massive traction and entered the mainstream, with most cloud and data center operators deploying it or planning to. There are countless success stories, but there are also challenges. Bringing security down to the application opens up a whole new series of questions – where should one begin? How will this be managed as applications change? These questions are exacerbated as applications become more distributed. And of course, how will the security evolve as the breaches are evolving?
VMware NSX pioneered micro-segmentation, using the virtualization layer as the ideal place to implement this critical defense capability. NSX is close enough to the application to gain valuable context and enforce granular security, yet separate enough from the application to isolate NSX from the attack surface (the app endpoint) in the event of a hack.
Introducing Context-Aware Micro-Segmentation
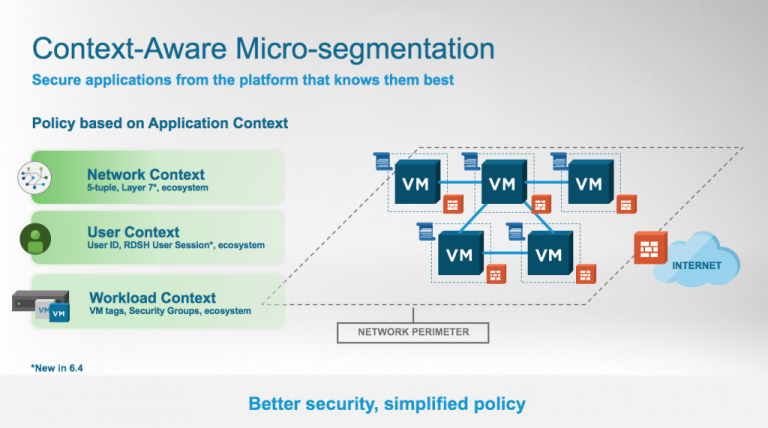
But the architectural advantages of NSX are only part of the story. Taking network security policies beyond just IP addresses and ports, NSX has been using attributes in the context of the application for years – VM name, OS version, regulatory scope, and more – to create policy. Not only is this approach more secure, it’s more manageable and can be easily automated, compared to policy based on constructs like IP addresses, which often change. With VMware NSX for vSphere 6.4, VMware takes this to a new level with Context-Aware Micro-segmentation, better securing applications using the full context of the application.
What’s New?
Much of the application context NSX uses has been supported for some time, so what’s new?
- Network flow app detection and enforcement at Layer 7 – while NSX tools like Endpoint Monitoring look within the application, the network layer should also be able to tell what application is running from its own unique position. With NSX for vSphere 6.4, NSX performs Deep Packet Inspection (past the TCP/UDP header) to identify the application in the network flow. This way, micro-segmentation policies from the network view don’t have to rely only on the 5-tuple information to infer what application it is. We’re starting with a core set of over fifty application signatures commonly found in east-west data center and cloud traffic which will grow over time. Think HTTP, SSH, DNS, etc.
- Virtual Desktop and Remote (RDSH) Session Security per User – one of the most popular starting points for micro-segmentation has been securing virtual desktops. It’s straightforward and locks down an otherwise vulnerable area – no traffic should flow between virtual desktops. In some environments, it’s simple to implement. But in many environments, multiple users are running desktop sessions on a single host. With the newest release, NSX can implement security in these environments based on the user and what they should be able to access. This also opens up this use case to a much broader variety of environments, including from Citrix and Microsoft.
Making Things Easier…
- Application Rule Manager – In addition to the policies being more intuitive and application driven, VMware is also spending a lot of time working on modeling around the people and processes involved in NSX deployments and the implementation of micro-segmentation, and we continue to add tools that help users be successful in their deployments. For example, there has been widespread use of vRealize Network Insight to gain broad visibility, helping users and administrators get the bigger picture of what’s going across the entire data center. Starting in NSX for vSphere 6.3, Application Rule Manager, then takes the allowed flows observed in the network and pushes policies directly into the distributed firewall within a few clicks. With NSX for vSphere 6.4, Application Rule Manager not only suggests rules, but also suggests application security groups to help build a more cohesive and manageable micro-segmentation strategy across the data center. One customer in the Beta program was using Application Rule Manager for the first time and found that it took them one-third of the time to micro-segment their applications.
Demo: Application Rule Manager
See Also: Application Rule Manager Practical Implementation – Healthcare
- Ease of use enhancements – You’ll also find integration with the HTML5 vSphere GUI, simplifying the GUI and representing an impactful step in an HTML5 journey, dashboard and logging enhancements, a completely redesigned upgrade experience with Upgrade Coordinator, and a long list of operational improvements you’ll find staring at you right from the release notes.
Demo: Upgrade Coordinator
A TON more…
As much as these security-focused NSX use cases have progressed, our favorite network virtualization platform has also added a whole suite of network-focused functionality too. In the same release notes you’ll see new routing features (NAT64 for IPv6 to IPv4 translation, BGP and static routing over GRE), JSON support for custom automation, multi-site enhancements with CDO, a host of scale improvements, resiliency improvements (BFD, ESG failover, L3VPN failover), health check monitors, and too much more to list here. You’ll want to check back on this blog in the coming weeks as we continue to unpack the goodness of NSX for vSphere 6.4.
As security threats continue to evolve, so must our defenses. Yet, increasing the sophistication of our security controls is only half the battle. It also needs to be simple to deploy and manage to be able to operationalize at scale. VMware NSX for vSphere 6.4 was developed with these two goals in mind. Kudos to our customers who have engaged with us and provided invaluable feedback that has driven much of the innovation in NSX for vSphere 6.4, now generally available. We look forward to continuing working with you all as we progress along this journey.
Category: News

No comments yet